
























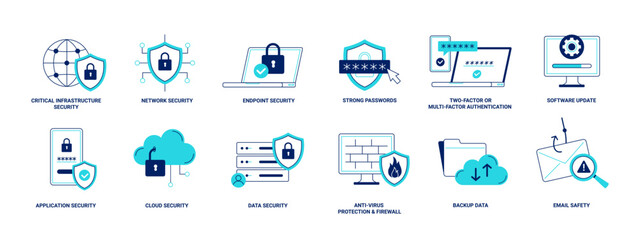





































































cyberspace online
Wall muralsecurity technology system
Wall muraldigital datum computer
Wall muralinformation network business
Wall muralcyber concept privacy
Wall muralaccess connection screen
Wall muralpassword protect safe
Wall muralcommunication server lock
Wall muralcyberspace
Wall muralonline
Wall muralsecurity
Wall muraltechnology
Wall muralsystem
Wall muraldigital
Wall muraldatum
Wall muralcomputer
Wall muralinformation
Wall muralnetwork
Wall muralbusiness
Wall muralcyber
Wall muralconcept
Wall muralprivacy
Wall muralaccess
Wall muralconnection
Wall muralscreen
Wall muralpassword
Wall muralprotect
Wall muralsafe
Wall muralcommunication
Wall muralserver
Wall murallock
Wall muraloffice
Wall murallaptop
Wall mural