







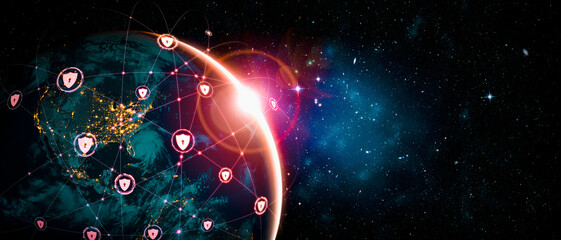






















































































cyberspace cyber
Wall muraltechnology online digital
Wall muralcomputer network security
Wall muraldatum business web
Wall muralinformation communication privacy
Wall muralsystem laptop secure
Wall muralconnection screen attack
Wall muralsoftware icon illustration
Wall muralcyberspace
Wall muralcyber
Wall muraltechnology
Wall muralonline
Wall muraldigital
Wall muralcomputer
Wall muralnetwork
Wall muralsecurity
Wall muraldatum
Wall muralbusiness
Wall muralweb
Wall muralinformation
Wall muralcommunication
Wall muralprivacy
Wall muralsystem
Wall murallaptop
Wall muralsecure
Wall muralconnection
Wall muralscreen
Wall muralattack
Wall muralsoftware
Wall muralicon
Wall muralillustration
Wall muralwebsite
Wall muralidentity
Wall mural