




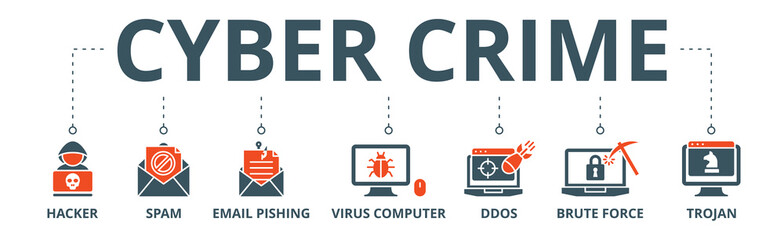



















































































identity criminal
Wall muralprotection security crime
Wall muraldatum privacy technology
Wall muralhacker cyber digital
Wall muralsafety network thief
Wall muralthieving concept password
Wall muralonline spy attack
Wall muraldanger system virus
Wall muralidentity
Wall muralcriminal
Wall muralprotection
Wall muralsecurity
Wall muralcrime
Wall muraldatum
Wall muralprivacy
Wall muraltechnology
Wall muralhacker
Wall muralcyber
Wall muraldigital
Wall muralsafety
Wall muralnetwork
Wall muralthief
Wall muralthieving
Wall muralconcept
Wall muralpassword
Wall muralonline
Wall muralspy
Wall muralattack
Wall muraldanger
Wall muralsystem
Wall muralvirus
Wall muralhacking
Wall murallaptop
Wall mural