

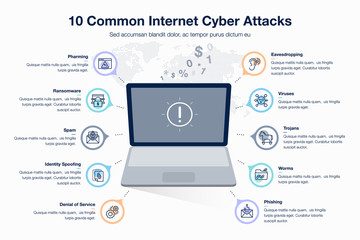


























































































cyberspace network
Wall muralcyber phishing security
Wall muralattack hacker technology
Wall muraldatum computer online
Wall muralpassword virus information
Wall muralprotection digital privacy
Wall muralhack threat safety
Wall muralfraud software scam
Wall muralcyberspace
Wall muralnetwork
Wall muralcyber
Wall muralphishing
Wall muralsecurity
Wall muralattack
Wall muralhacker
Wall muraltechnology
Wall muraldatum
Wall muralcomputer
Wall muralonline
Wall muralpassword
Wall muralvirus
Wall muralinformation
Wall muralprotection
Wall muraldigital
Wall muralprivacy
Wall muralhack
Wall muralthreat
Wall muralsafety
Wall muralfraud
Wall muralsoftware
Wall muralscam
Wall murallaptop
Wall muralaccess
Wall mural