




























































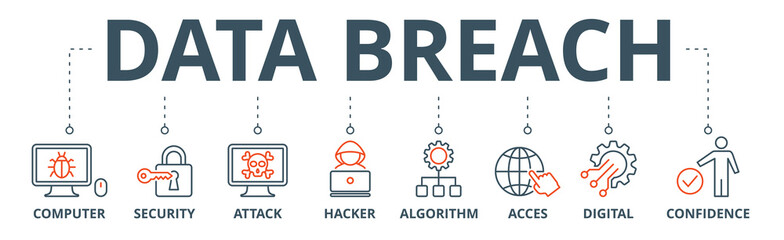


































cyberspace online
Wall muralcyber information security
Wall muralcomputer network business
Wall muralsystem web privacy
Wall muralprotection safety concept
Wall muralprotect secure password
Wall murallock software communication
Wall muralcode virus background
Wall muralcyberspace
Wall muralonline
Wall muralcyber
Wall muralinformation
Wall muralsecurity
Wall muralcomputer
Wall muralnetwork
Wall muralbusiness
Wall muralsystem
Wall muralweb
Wall muralprivacy
Wall muralprotection
Wall muralsafety
Wall muralconcept
Wall muralprotect
Wall muralsecure
Wall muralpassword
Wall murallock
Wall muralsoftware
Wall muralcommunication
Wall muralcode
Wall muralvirus
Wall muralbackground
Wall muralicon
Wall muralconnection
Wall mural