










































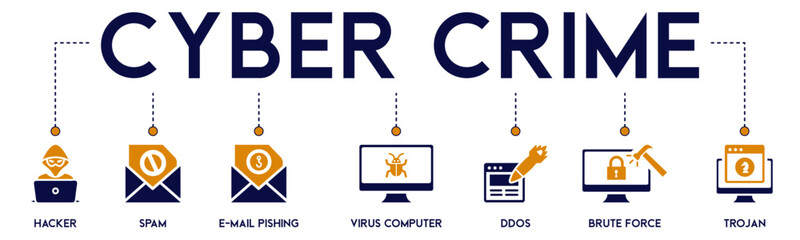


































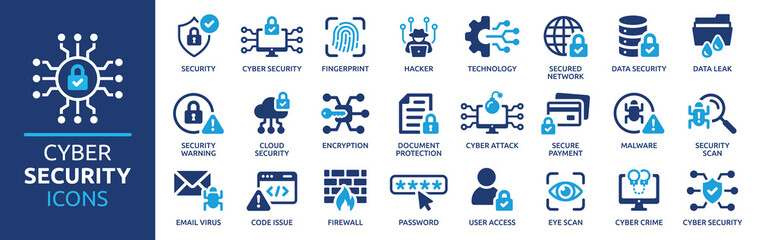







cyberspace virus
Wall muralcrime code technology
Wall muralhacker network digital
Wall muraldatum cyber attack
Wall muralhacking information web
Wall muralcriminal system binary
Wall muralpassword hack screen
Wall murallaptop danger background
Wall muralcyberspace
Wall muralvirus
Wall muralcrime
Wall muralcode
Wall muraltechnology
Wall muralhacker
Wall muralnetwork
Wall muraldigital
Wall muraldatum
Wall muralcyber
Wall muralattack
Wall muralhacking
Wall muralinformation
Wall muralweb
Wall muralcriminal
Wall muralsystem
Wall muralbinary
Wall muralpassword
Wall muralhack
Wall muralscreen
Wall murallaptop
Wall muraldanger
Wall muralbackground
Wall muralphishing
Wall muralprotection
Wall mural