




































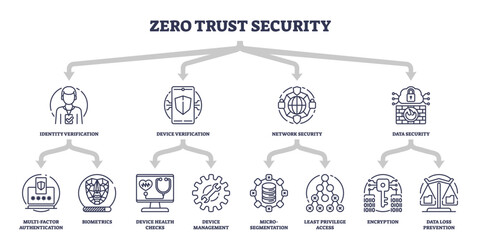











































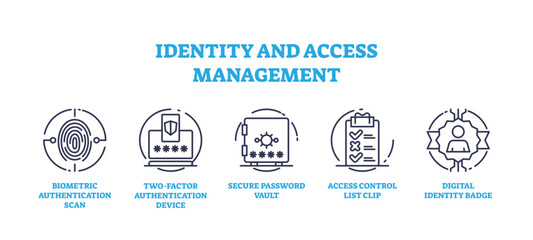














access protection
Wall muralmanagement security technology
Wall muraldatum network privacy
Wall muralsystem control encryption
Wall muralinformation secure identity
Wall muralsafety authentication software
Wall muralcyberspace firewall monitor
Wall muralprevention protocol service
Wall muralaccess
Wall muralprotection
Wall muralmanagement
Wall muralsecurity
Wall muraltechnology
Wall muraldatum
Wall muralnetwork
Wall muralprivacy
Wall muralsystem
Wall muralcontrol
Wall muralencryption
Wall muralinformation
Wall muralsecure
Wall muralidentity
Wall muralsafety
Wall muralauthentication
Wall muralsoftware
Wall muralcyberspace
Wall muralfirewall
Wall muralmonitor
Wall muralprevention
Wall muralprotocol
Wall muralservice
Wall muralinnovation
Wall muralconcept
Wall mural